Last Updated : 29 Aug, 2024
Summarize
Comments
Improve
Blockchain technology often heralded as a revolutionary advancement, fundamentally transforms how data is stored, managed, and verified across distributed networks. At its core, a blockchain is a decentralized digital ledger that maintains a continuous and immutable record of transactions across a network of computers. The structure of a blockchain is crucial to its functionality and security. This article focuses on discussing the Blockchain structure in detail.
Table of Content
- What is Blockchain?
- Core Components of Blockchain
- Data Storage and Management
- Types of Blockchain
- Consensus Mechanisms in Blockchain
- Cryptographic Foundations in Blockchain
- Smart Contracts and Decentralized Applications (DApps)
- Blockchain Architecture Vs Database
- Security Challenges in Blockchain Structures
- Best Practices for Enhancing Blockchain Security
- Conclusion
- FAQs
What is Blockchain?
Blockchain is a technology where multiple parties involved in communication can perform different transactions without third-party intervention. Special nodes verify and validate these transactions.
Features of Blockchain
- Decentralization: In centralized transaction systems, each transaction must be validated in the central trusted agency (e.g., the central bank), naturally resulting in cost and performance jams at the central servers. In contrast to the centralized mode, a third party is not needed in the blockchain. Consensus algorithms in blockchain maintain data stability in a decentralized network.
- Persistency: Transactions can be validated quickly and invalid transactions would not be admitted by persons or miners who mining the crypto. It is not possible to delete or roll back transactions once they are included in the blockchain network. Invalid transactions do not carry forward further.
- Anonymity: Each user can interact with the blockchain with a generated address, which does not disclose the real identity
of the miner. Note that blockchain cannot guarantee perfect privacy preservation due to the permanent thing. - Auditability: Blockchain stores data of users based on the Unspent Transaction Output (UTXO) model.
Every transaction has to refer to some previous unspent transactions. Once the current transaction is recorded into the
blockchain, the position of those referred unspent transactions switches from unspent to spent. Due to this process, the transactions can be easily tracked and not harmed between transactions. - Transparency: The transparency of blockchain is like cryptocurrency, in Bitcoin for tracking every transaction is done by the address. For security, it hides the person’s identity between and after the transaction. All the transactions are made by the owner of the block associated with the address, this process is transparent and there is no loss for anyone who is involved in this transaction.
- Cryptography: The blockchain concept is fully based on security and for that, all the blocks on the blockchain network want to be secure. For security, it implements cryptography and secures the data using the cipher text and ciphers.
Core Components of Blockchain
- Node: Nodes are network participants and their devices permit them to keep track of the distributed ledger and serve as communication hubs in various network tasks. A block broadcasts all the network nodes when a miner looks to add a new block in transactions to the blockchain.
- Transactions: A transaction refers to a contract or agreement and transfers of assets between parties. The asset is typically cash or property. The network of computers in blockchain stores the transactional data as a copy with the storage typically referred to as a digital ledger.
- Block: A block in a blockchain network is similar to a link in a chain. In the field of cryptocurrency, blocks are like records that store transactions like a record book, and those are encrypted into a hash tree. There are a huge number of transactions occurring every day in the world. The users need to keep track of those transactions, and they do it with the help of a block structure. The block structure of the blockchain is mentioned in the very first diagram in this article.
- Chain: Chain is the concept where all the blocks are connected with the help of a chain in the whole blockchain structure in the world. And those blocks are connected with the help of the previous block hash and it indicates a chaining structure.
- Miners: Blockchain mining is a process that validates every step in the transactions while operating all cryptocurrencies. People involved in this mining they called miners. Blockchain mining is a process to validate each step in the transactions while operating cryptocurrencies.
- Consensus: A consensus is a fault-tolerant mechanism that is used in computer and blockchain systems to achieve the necessary agreement on a single state of the network among distributed processes or multi-agent systems, such as with cryptocurrencies. It is useful in record keeping and other things.
Data Storage and Management
- Header: It is used to identify the particular block in the entire blockchain. It handles all blocks in the blockchain. A block header is hashed periodically by miners by changing the nonce value as part of normal mining activity, also Three sets of block metadata are contained in the block header.
- Previous Block Address/ Hash: It is used to connect the i+1th block to the ith block using the hash. In short, it is a reference to the hash of the previous (parent) block in the chain.
- Timestamp: It is a system that verifies the data into the block and assigns a time or date of creation for digital documents. The timestamp is a string of characters that uniquely identifies the document or event and indicates when it was created.
- Nonce: A nonce number which used only once. It is a central part of the proof of work in the block. It is compared to the live target if it is smaller or equal to the current target. People who mine, test, and eliminate many Nonce per second until they find that Valuable Nonce is valid.
- Merkel Root: It is a type of data structure frame of different blocks of data. A Merkle Tree stores all the transactions in a block by producing a digital fingerprint of the entire transaction. It allows the users to verify whether a transaction can be included in a block or not.
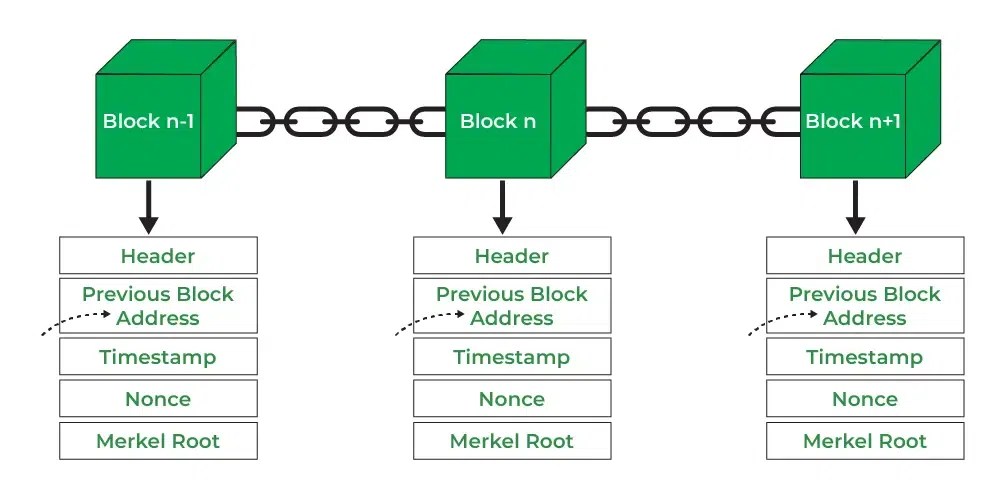
Blockchain Structure
Types of Blockchain
1. Public Blockchain
A public blockchain is a concept where anyone is free to join and take part in the core activities of the blockchain network. Anyone can read, write, and audit the ongoing activities on a public blockchain network, which helps to achieve the self-determining, decentralized nature often authorized when blockchain is discussed. Data on a public blockchain is secure as it is not possible to modify once they are validated.
The public blockchain is fully decentralized, it has access and control over the ledger, and its data is not restricted to persons, is always available and the central authority manages all the blocks in the chain. There is publicly running all operations. Due to no one handling it singly then there is no need to get permission to access the public blockchain. Anyone can set his/her node or block in the network/ chain.
After a node or a block settles in the chain of the blocks, all the blocks are connected like peer-to-peer connections. If someone tries to attack the block then it forms a copy of that data and it is accessible only by the original author of the block.

Public Blockchain
Advantages:
- Decentralization: High level of decentralization, which reduces the risk of single points of failure and increases security.
- Transparency: All transactions are visible to anyone, enhancing transparency and trust.
- Immutability: Once data is recorded, it cannot be altered or deleted, providing a permanent record.
Disadvantages:
- Scalability Issues: Public blockchains often face scalability problems, with limited transaction throughput and slower processing times.
- Energy Consumption: Some consensus mechanisms, like Proof of Work (PoW), require significant computational power and energy.
- Privacy Concerns: Public visibility of transactions may lead to privacy issues, as sensitive data can be exposed.
2. Private Blockchain
Miners need permission to access a private blockchain. It works based on permissions and controls, which limit participation in the network. Only the entities participating in a transaction will know about it and the other stakeholders not be able to access it.
It works based on permissions due to this it is also called a permission-based blockchain. Private blockchains are not like public blockchains it is managed by the entity that owns the network. A trusted person is in charge of the running of the blockchain it will control who can access the private blockchain and also control the access rights of the private chain network. There may be a possibility of some restrictions while accessing the network of the private blockchain.

Private Blockchain
Advantages:
- Performance and Speed: Faster transaction processing and higher throughput compared to public blockchains due to fewer nodes and reduced consensus requirements.
- Privacy: Transactions and data are visible only to authorized participants, enhancing privacy.
- Control: Centralized control allows for easier governance and compliance with regulations.
Disadvantages:
- Centralization: Less decentralized than public blockchains, which can introduce single points of failure and reduce the security benefits.
- Trust: Requires participants to trust the central authority or consortium managing the blockchain.
- Limited Transparency: Reduced transparency can make it harder for external auditors to verify data.
3. Consortium Blockchain
A consortium blockchain is a concept where it is permissioned by the government and a group of organizations, not by one person like a private blockchain. Consortium blockchains are more decentralized than private blockchains, due to being more decentralized it increases the privacy and security of the blocks. Those like private blockchains connected with government organizations’ block networks.
Consortium blockchains lie between public and private blockchains. They are designed by organizations and no one person outside of the organizations can gain access. In Consortium blockchains all companies in between organizations collaborate equally. They do not give access from outside of the organizations/ consortium network.
Advantages:
- Efficiency: Better performance and efficiency than public blockchains due to fewer nodes and optimized consensus mechanisms.
- Shared Control: Governance is shared among consortium members, which can enhance trust and cooperation.
- Privacy and Security: Improved privacy and security compared to public blockchains, as access is restricted.
Disadvantages:
- Complex Governance: Decision-making can be complex due to multiple stakeholders with potentially conflicting interests.
- Less Decentralization: While more decentralized than private blockchains, consortium blockchains still have a limited number of participants, which can reduce some decentralization benefits.
- Interoperability: Challenges can arise when integrating with other blockchain networks or systems.
4. Hybrid Blockchain
Hybrid blockchains combine elements of both public and private blockchains. They aim to offer the benefits of both types, allowing for controlled access and transparency. Examples include Dragonchain and IBM’s Food Trust.
Advantages:
- Flexibility: Offers the ability to balance transparency and privacy based on the needs of the organization or project.
- Scalability and Performance: Can be designed to optimize performance and scalability while maintaining some degree of transparency.
- Customizable Access: Allows organizations to control who can access certain data while making some data available to the public.
Disadvantages:
- Complexity: Implementation can be more complex due to the need to manage different access levels and integrations.
- Governance Challenges: Balancing governance between public and private aspects can be challenging.
- Potential for Confusion: This mayrequires lead to confusion among users and stakeholders about the nature and scope of access and transparency.
Consensus Mechanisms in Blockchain
There are different kinds of consensus mechanism algorithms, each of which works on different principles:
- Proof of Work (PoW): Proof of Work requires a stakeholder node to prove that the work is done and submitted by them certifying them to receive the right to add new transactions in the blockchain. Examples include Bitcoin and Ethereum (before Ethereum 2.0).
- Proof of Stake (PoS): The Proof of Stake is also a common consensus algorithm that evolved as a low-cost low-energy-consuming, low-energy-consuming alternative for the PoW algorithm. For providing the responsibilities the public ledger provides by the virtual currency token like Bitcoin and Ethereum. Examples include Ethereum 2.0 and Cardano.
- Proof of Elapsed Time (PoET): PoET encrypts the passage of time cryptographically to reach an agreement without expending many resources.
- Delegated Proof of Stake (DPoS): Stakeholders elect a limited number of delegates to validate transactions and create blocks on their behalf. It has higher transaction throughput and faster block creation. In DPoS, risk of centralization and reliance on elected delegates. Examples include EOS and TRON.
- Proof of Authority (PoA): A small number of pre-approved validators are responsible for creating blocks and validating transactions. PoA has high efficiency and low energy consumption. There is a risk of centralization and dependency on the trustworthiness of validators. Examples include VeChain and private Ethereum networks.
- Practical Byzantine Fault Tolerance (PBFT): In PBFT, nodes reach consensus through voting, even if some nodes act maliciously or fail. It is effective in handling Byzantine faults and offers fast transaction processing. There is a complexity in scaling to large networks. Examples include Hyperledger Fabric.
Cryptographic Foundations in Blockchain
Cryptography is important to the security and functionality of blockchain technology. Here is an overview of the key cryptographic foundations used in blockchain:
- Hash Functions: Hash functions are algorithms that generate a fixed-size output (hash) from variable-size input data. They are designed to be fast and produce unique outputs for different inputs. Hash functions are used to create block hashes, ensuring the integrity of the data within the block and linking blocks together in the chain. Examples include SHA-256 used in Bitcoin.
- Digital Signatures: Digital signatures use asymmetric cryptography to verify the authenticity and integrity of messages or transactions. They involve a private key to sign data and a public key to verify the signature. Digital signatures secure transactions by allowing users to sign transactions with their private keys and enabling others to verify these signatures with the corresponding public keys. Examples include the Elliptic Curve Digital Signature Algorithm (ECDSA) used in Bitcoin and Ethereum.
- Public and Private Keys: In asymmetric cryptography, a key pair consists of a public key, which is shared with others, and a private key, which is kept secret. The public key encrypts data, and the private key decrypts it, or vice versa. Public and private keys are fundamental for creating and managing wallets, securing transactions, and authenticating users on the blockchain. Examples include RSA (Rivest-Shamir-Adleman), ECC (Elliptic Curve Cryptography), etc.
- Merkle Trees: Merkle trees are a type of hash tree where each leaf node represents a hash of data, and each non-leaf node represents a hash of its child nodes. They are used to efficiently and securely verify the integrity of large sets of data. Merkle trees are used to organize and verify transactions within a block, allowing for efficient and secure validation. Examples include the Merkle root in Bitcoin blocks.
Smart Contracts and Decentralized Applications (DApps)
Here is an overview of smart contracts and dApps in blockchain systems:
Smart Contracts
Smart contracts are self-executing contracts with the terms of the agreement directly written into code. They automatically execute, enforce, and verify the conditions of a contract without the need for intermediaries.
Key Features:
- Automation: Automatically performs actions (e.g., transferring assets) when predefined conditions are met.
- Transparency: Code and execution are visible on the blockchain, ensuring all parties can verify the contract’s operation.
- Immutability: Once deployed, smart contracts cannot be altered, providing a secure and tamper-proof execution environment.
Usage:
- Financial Agreements: Automating complex financial transactions such as loans, insurance claims, or trading agreements.
- Supply Chain: Tracking and verifying the movement and provenance of goods.
- Governance: Implementing rules and governance structures in decentralized organizations or DAOs.
Examples:
Ethereum’s ERC-20 and ERC-721 tokens use smart contracts to define token standards and manage transactions.
Decentralized Applications (DApps)
DApps are applications that run on a decentralized network, typically a blockchain. They leverage smart contracts to operate autonomously and ensure transparency and security.
Key Features:
- Decentralization: Operate on a peer-to-peer network rather than a centralized server, distributing data and processing across multiple nodes.
- Trustless Interaction: Users interact directly with the application and smart contracts without needing to trust a central authority.
- Open Source: Often open source, allowing for transparency and community collaboration in development.
Usage:
- Financial Services: Decentralized finance (DeFi) platforms for lending, borrowing, and trading cryptocurrencies.
- Gaming: Blockchain-based games that use NFTs for in-game assets and rewards.
- Social Networks: Platforms where users retain control over their data and content.
Example:
Uniswap is a decentralized exchange (DEX) that allows users to trade cryptocurrencies without relying on a central authority.
Blockchain Architecture Vs Database
Below are some of the differences between blockchain architecture and database:
| Parameters | Blockchain Architecture | Database |
|---|---|---|
| Control | Blockchain is decentralized because there is no single point of failure and there is no central authority to control the blockchain. | The database is Centralized. |
| Operations | Blockchain has only an Insert operation. | The database has Create, Read, Update, and Delete operations. |
| Strength | It is robust technology. | The database is not fully robust technology. |
| Mutability | Blockchain is an immutable technology and we cannot change it or we cannot go back. | The database is a fully mutable technology, The data can be edited in the database. |
| Rights | Anyone with the right proof of work can write on the blockchain. | In the database reading and writing can do so. |
| Speed | It is slow. | It is faster as compared to blockchain. |
Security Challenges in Blockchain Structures
Here are some key security challenges in blockchain structures:
- 51% Attacks: If a single entity or group controls more than 50% of the network’s computational power (in PoW) or stake (in PoS), they can potentially manipulate the blockchain by double-spending, halting transactions, or reversing transactions. 51% attacks can be mitigated by increasing network size, using consensus mechanisms resistant to centralization, and incorporating additional security layers.
- Sybil Attacks: An attacker creates multiple fake identities (nodes) to gain disproportionate influence over the network. In PoW, this involves creating numerous fake mining nodes; in PoS, it involves acquiring a large amount of stake from multiple fake accounts. This can disrupt network consensus, compromise the integrity of the blockchain, and skew decision-making processes. Sybil attacks can be mitigated by implementing identity verification and reputation systems and utilizing robust consensus mechanisms.
- Double Spending: A form of fraud where a digital currency or asset is spent more than once. This typically occurs when an attacker manages to alter the blockchain history or exploit network delays. This results in financial loss and undermines trust in the blockchain’s ability to securely manage transactions. Double spending can be mitigated by employing consensus mechanisms to ensure transaction finality and using transaction confirmation strategies to detect and prevent double spending.
- Smart Contract Vulnerabilities: Flaws or bugs in smart contracts can lead to unintended behaviors or security breaches. Common issues include reentrancy attacks, integer overflows/underflows, and logic errors. This can lead to loss of funds, unauthorized access, and exploitation of contract logic. These can be mitigated by conducting thorough code audits, using formal verification methods, and following best practices in smart contract development.
- Network Partitioning (Eclipse Attacks): An attacker isolates a node from the rest of the network, feeding it false or malicious information to manipulate its view of the blockchain. This can lead to incorrect transaction validation, loss of consensus, and disruptions in the network’s functionality. Eclipse attacks can be mitigated by enhancing network connectivity, implementing robust peer discovery protocols, and monitoring for unusual network behaviors.
- Endpoint Security: The security of endpoints (e.g., user devices, wallets) is crucial, as vulnerabilities can lead to unauthorized access to private keys and other sensitive information. This can result in theft of assets, unauthorized transactions, and loss of control over blockchain assets. Endpoint security can be taken care of by encouraging best practices in device security, using hardware wallets, and implementing strong authentication measures.
Best Practices for Enhancing Blockchain Security
Here are key best practices to enhance blockchain security:
- Regular Code Audits: Conduct thorough and regular audits of blockchain code, especially smart contracts. Engage with reputable security firms or experts to perform comprehensive code reviews and testing.
- Use of Strong Cryptographic Techniques: Employ robust cryptographic algorithms and protocols to secure data. Use well-established algorithms like SHA-256 for hashing and ECDSA for digital signatures, and stay updated on cryptographic advancements.
- Implement Multi-Signature Wallets: Use multi-signature (multi-sig) wallets that require multiple signatures to authorize transactions. Configure multi-sig wallets based on organizational needs, such as requiring approvals from multiple executives or stakeholders.
- Adopt Secure Development Practices: Follow best practices in software development to minimize vulnerabilities. Implement secure coding practices, conduct threat modeling, and use development frameworks that emphasize security.
- Enhance Endpoint Security: Secure all endpoints interacting with the blockchain, including user devices and servers. Use antivirus software, and firewalls, and ensure devices are kept up-to-date with security patches.
- Implement Access Controls and Permissions: Use strict access controls to manage who can interact with and modify blockchain components. Implement role-based access controls (RBAC) and enforce least privilege principles.
Conclusion
In conclusion, blockchain technology offers a powerful way to securely and transparently record transactions and data through its decentralized, immutable ledger. By organizing data into blocks linked together in a chain, blockchain ensures that once information is added, it cannot be altered or deleted. This structure provides enhanced security, trust, and integrity across various applications, from cryptocurrencies to supply chain management. As blockchain continues to evolve, its foundational principles of decentralization, transparency, and cryptographic security will remain crucial to its effectiveness and reliability.
FAQs
1. What is the purpose of hashing in a blockchain?
Hashing is used to create a unique, fixed-size string of characters (hash) for each block based on its content. This process secures the block’s data and links it to the previous block, ensuring that any change in the block’s data will alter its hash and alert the network to potential tampering.
2. How is data stored and secured in a blockchain?
Data in a blockchain is stored in blocks that are linked together in a chain. Each block contains a list of transactions, a timestamp, and a cryptographic hash of the previous block. This structure ensures data integrity and security by making it nearly impossible to alter any data without changing subsequent blocks.
3. How can blockchain networks prevent attacks?
Blockchain networks can prevent attacks through various measures, including Robust Consensus Mechanisms, Regular Code Audits, and Network Monitoring.
Previous Article
practical Byzantine Fault Tolerance(pBFT)
Next Article
Candidate block in Blockchain
