SSH keys not only improve security but also enable the automation of connected processes, single sign-on (SSO), and identity and access management at scale that today’s businesses require.
Table of Contents
1. What is an SSH key?
2. How do SSH keys work?
3. SSH public key authentication vs. passwords
4. Where to find your SSH keys
5. How to generate an SSH key pair
6. Configuring SSH
7. SSH key management
What is an SSH key?
updated on: 01.22.2024
An SSH key is a secure access credential used in the Secure Shell (SSH) protocol. SSH key pairs use public key infrastructure (PKI) technology, the gold standard for digital identity authentication and encryption, to provide a secure and scalable method of authentication.
As the SSH protocol is widely used for communication in cloud services, network environments, file transfer tools, configuration management tools, and other computer-dependent services, most organizations use this type of key-based authentication to verify identities and protect those services from unintended use or malicious attacks.
Key pair - public and private keys
An SSH key relies upon the use of two related but asymmetric keys, a public key and a private key, that together create a key pair that is used as the secure access credential. The private key is secret, known only to the user, and should be encrypted and stored safely. The public key can be shared freely with any SSH server to which the user wishes to connect. These keys are normally managed by an organization’s IT team, or better yet, with the help of a trusted Certificate Authority (CA) to ensure they are stored safely.
To create the digital identity, the public and private key are both generated, and the pair is associated with each other using a strong public key cryptography algorithm. The most common mathematical algorithms used for key generation are Rivest–Shamir–Adleman (RSA) and Elliptic Curve Digital Signature Algorithm (ECDSA), which is an elliptic curve application of DSA.
These algorithms use various computation methods to generate random numeric combinations of varying length so that they cannot be exploited with a brute force attack. The key size or bit length helps determine the strength of protection. 2048-bit RSA keys or 521-bit ECDSA keys offer sufficient cryptographic strength to keep hackers from cracking the algorithm.
How do SSH keys work?
The SSH key pair is used to authenticate the identity of a user or process that wants to access a remote system using the SSH protocol. The public key is used by both the user and the remote server to encrypt messages. On the remote server side, it is saved in a public key file. On the user’s side, it is stored in SSH key management software or in a file on their computer. The private key remains only on the system being used to access the remote server and is used to decrypt messages.
When a user or process requests a connection to the remote server using the SSH client, a challenge-response sequence is initiated to complete authentication. The SSH server recognizes that a connection is being requested and sends an encrypted challenge request using the shared public key information. The SSH client then decrypts the challenge message and responds back to the server. The user or process must respond correctly to the challenge to be granted access. This challenge-response sequence happens automatically between the SSH client and server without any manual action by the user.
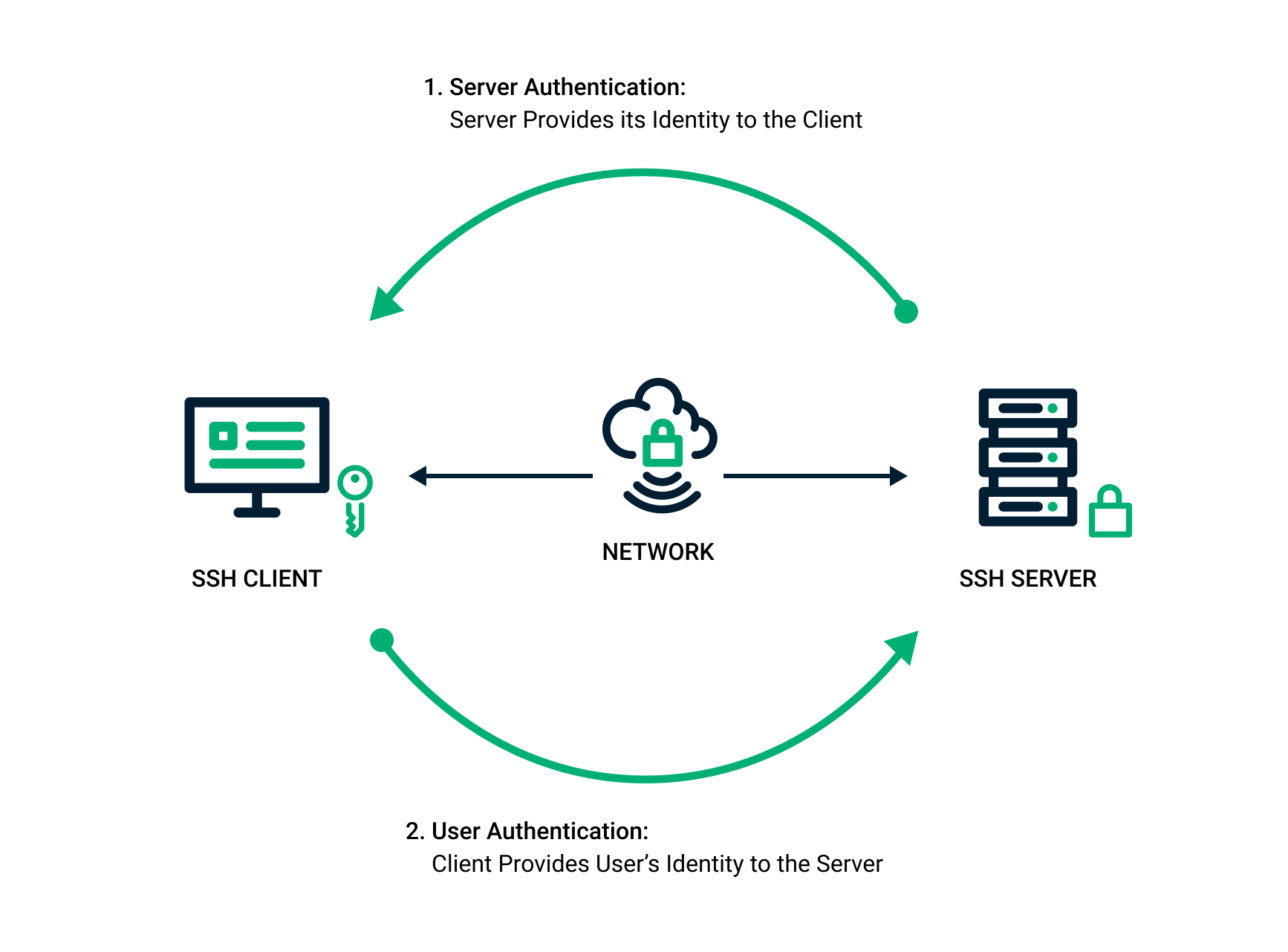
SSH public key authentication vs. passwords
At a high level, SSH keys function like passwords by controlling access. But that’s where the similarity ends. Digital identities need to be strong so that they cannot be stolen, convenient so that access is fast and never interrupted, and future-proof so that enterprises can stay ahead of possible threats.
Passwords used to offer a measure of security, but they are not as effective as they once were. That’s because bad actors have become increasingly adept at stealing passwords in transit through the internet, lifting them from repositories, and obtaining them through brute force attacks.
These security risks and issues are compounded by the human factor: that people reuse, share, and continually forget passwords. The cost to businesses is high, not only because of data loss, outages, and the compromise of information, but also because passwords take time to enter, require significant support resources, and must be frequently reset.
Using PKI's cryptographic strength and authentication methods, SSH keys are not prone to malicious attacks and valid credentials are not exposed if a server has been compromised. PKI cryptography is being improved continuously, future-proofing identities against new and evolving threats.
SSH key authentication is also more convenient than password authentication. The keys connect users and processes to a server by initiating authentication and granting access automatically, so users don’t have to remember or enter their password for each and every system.
That being said, you should always password-protect your SSH private keys, or store them on a hardware token for added security.
Where to find your SSH keys
Before you’re able to use SSH keys, you will want to check to make sure your user account has them and if not, they will need to be created. There are several ways to do this, such as using Yubikeys or other hardware security solutions, which are often the safest way to go. However, for a more basic setup, you can use the .ssh directory.
If you opt to use the .ssh directory, you can find your SSH key pair by following these steps:
Go to your personal directory and look for the SSH directory. For Linux and MacOS, the default location is the ~/.ssh directory. On Windows, the default is C:\Users\<username>\.ssh.
Look for two files named something similar to id_dsa or id_rsa. One will have the .pub extension and the other will not (e.g., id_rsa.pub and id_rsa). The .pub file is the public key and the other is the private key. The public key may not always be present as it is not required on the client in order to work.
If you don’t find these files in the directory, or you don’t have a directory at all, then you will need to create the SSH keys.
How to generate an SSH key pair
To generate the SSH public/private key pair, one can do this manually or use an automated certificate management system.
Generating and storing new SSH keys manually can be accomplished on the most common operating systems. On Windows systems, they can be generated using the ssh-keygen command line tool or an SSH client, like PuTTy. On MacOs and Linux systems, they are generated using a terminal window.
To generate an SSH key, complete the following command line steps:
Enter the key gen command $ ssh-keygen -t rsa
Enter file in which to save the keys. Typically, the keys stored in the home directory or ~/.ssh/ directory (e.g. /home/foldername/.ssh/id_rsa or /c/Users/username/.ssh/id_rsa). Press enter once the preferred file name is chosen.
Enter a passphrase or leave empty for no passphrase. Note: The passphrase provides an additional layer of password protection for the key pair, but the user must type in the passphrase each time the key pair is used.
Once the pair is generated, the next step is to put the public key on the remote server. A system administrator can copy the SSH public key into the remote server’s authorized_keys file using the ssh-copy-id command (e.g. $ ssh-copy-id username@IP address). Alternatively, you can paste in the keys using secure shell command (e.g. $ cat ~/.ssh/id_rsa.pub | ssh username@IP address "mkdir -p ~/.ssh && chmod 700 ~/.ssh && cat >> ~/.ssh/authorized_keys").
These steps then allow you to use the private key file for SSH authentication.
Configuring SSH
You can configure SSH by modifying the system-wide configuration file on the server. Generally the file name is /etc/ssh/sshd_config.
Once you access the /etc/ssh/sshd_config file, you can use it to control which users and which groups have SSH access to the server.
Similarly, local client configuration can be done in a .ssh/config file. Through this file, a user can add specific configuration on a per-host basis, including, but not limited to, setting which private key to use for which server, which username and set-up SSH Tunnels.
SSH key management
Proper SSH key management is essential for organizations as these keys grant access to mission-critical business systems and data. Yet, managing them manually can be time-consuming and prone to error. It is further complicated by the fact that organizations typically have thousands, if not millions of keys stored throughout their environment. The security they provide can easily be undermined if configuration, provisioning, and termination policies are not in place and actively managed.
For example, when issued keys are no longer needed, as in the case when employees leave an organization, IT staff may forget to terminate them. Discovery of such orphaned keys is almost impossible, which creates a risk that they exist on systems that are not closely controlled. If these orphaned keys are unprotected, they can be stolen by a malicious actor, who can then use the still active credentials to access your critical business systems and data.
Dedicated SSH key management solutions using the ssh-agent helper program are available to provision, configure, and terminate keys. Using these solutions is significantly better than managing manually, but this approach requires busy IT staff to use another management tool in addition to their existing security and administrative solutions. Instead, IT teams should use a centralized certificate management solution that automatically manages all PKI-based certificates. Leveraging a singular approach to certificate management allows IT staff to complete all of their key management tasks in one dashboard.
