Ciphers are a big part of cybersecurity – they maintain security and privacy on phones, websites, digital television, and even ATMs. In cryptography, ciphertext is a type of secret code that differs from encryption, although the two are closely related and intertwined.
What is Ciphertext?
Ciphertext is simply plain text – that is, any ordinary text – that is encrypted. Its purpose is to become unreadable to most people by utilizing an algorithm called a cipher. The cipher is the tool used to encrypt plain text.
What’s the Difference Between Ciphertext and Plain Text?
Plain text is any bit of ordinary writing that can be read and understood using normal language. Ciphertext transforms plain text utilizing encryption so that it can no longer be understood in ordinary terms. This encryption results in ciphertext appearing as a set of randomized numbers and letters that are incomprehensible to the untrained eye. However, if you know and understand the decryption code, the ciphertext can be translated.

What’s an Example of a Ciphertext?
There are many different types of ciphertexts, all of which use different encryptions. However, if you’re wondering what it may look like, here’s an example for you:
The Caesar cipher is one of the most straightforward types of ciphertext. Each letter in question is shifted one place down the alphabet - meaning A becomes B and B becomes C, just like L becomes M and V becomes W. Using this rule, the plain text is then transformed into a jumble of letters that cannot be read without knowing the cipher.
An Example of a Caesar Cipher
Plain text: Jack and Jill went up the hill
Ciphertext: Kbdl boe Kjmm xfou vq uif ijmm
Without understanding the encryption code, the above text is incomprehensible. However, if you understand the type of cipher that has been used, you can easily make the translation.
Why is Ciphertext Used?
Cybersecurity uses ciphertext in almost all its functions - by preventing data and confidential information from being shared and understood by those who shouldn’t have access to it.
While there are many other layers of cybersecurity that are focused on preventing unauthorized access to data, the use of ciphers protects data even when outsiders can view it. It acts as an additional level of defense if hackers can successfully infiltrate your system as they still won’t be able to make sense of the actual data or information they find.
An encryption key acts as a code to ensure that the plain text becomes unreadable. Conversely, a decryption code is the key that unlocks the cipher - making it accessible and understandable to ordinary people.
When it comes to asymmetric encryption, also known as public-key encryption, there are two types of keys.
The key uses are very strict and specific. A public key can only be used to encode data and transform it from plain text to a cipher, while a private key can only be used to decode data and transform it from ciphertext back into ordinary language.
What’s the Difference Between Ciphertext and Encryption?
While the two processes are very closely related to each other, they’re not quite the same.
A cipher is an algorithm that is applied to plain text in order to produce coded text – that is, ciphertext. Encryption, on the other hand, refers to the actual conversion process whereby data is transformed utilizing a cipher.
Therefore, a ciphertext is produced through the process of encryption.
Types of Ciphers
There are two main types of ciphers – block ciphers and stream ciphers. But what’s the difference between the two?
Block Ciphers
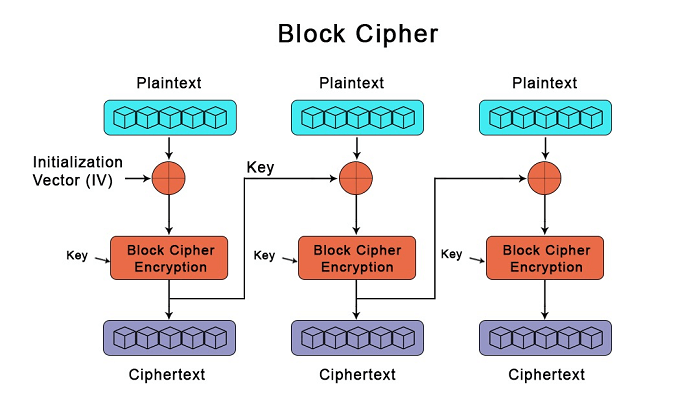
Source:https://www.javatpoint.com/block-cipher-vs-stream-cipher
Block ciphers focus on collections, or rather blocks of data that are fixed in size and measured in bits. Entire blocks are encrypted at a time using a symmetric key. The length of the block influences the ease or difficulty at which the cipher may be cracked – the longer, the better.
An Example of a block cipher:
One of the most secure forms of encryption, AES encryption, requires the recipient of the ciphertext to have the correct key in order to access the plain text within the encrypted data.
Block ciphers are commonly used by governments and virtual private networks of organizations holding highly confidential information that needs to be protected.
Stream Ciphers
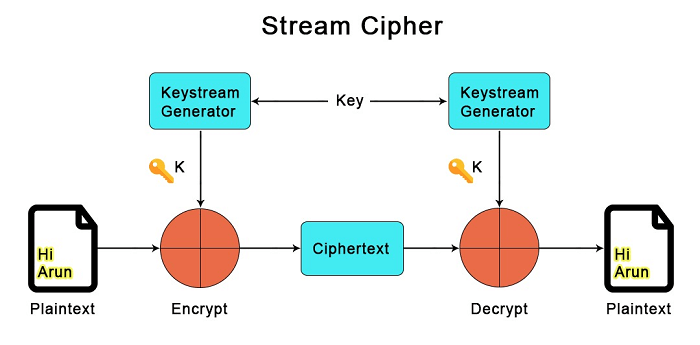
Source:https://www.javatpoint.com/block-cipher-vs-stream-cipher
Stream ciphers deal with continuous streams of data in order to encrypt them. They encrypt plain text bit by bit by applying an encryption algorithm – a cipher – with a pseudorandom cipher digit stream, which is also known as a key stream.
An Example of a stream cipher:
Stream ciphers are best used in cases where speed and simplicity are important. For instance, secure wireless connections wherein the plain text in question is of a length that is unknown.
Other Types of Ciphers
- Polygraphic ciphers:Plain text is divided into different parts, and each part is assigned a word, a character, a symbol, or any other group of agreed-upon characters.
- Permutation ciphers:Permutation ciphers rely on the order of the characters or groups of characters. In order to create a permutation cipher, the linear arrangement of characters is shuffled so that the order is changed. For instance, “January, February, March” may be changed to “February, March, January.”
- Transposition ciphers:Units of the plain text are reorganized according to a chosen system. If you’re changing the order of letters in a series of words, however, the order of the whole words stays the same.
- Substitution ciphers:Substitution ciphers allow units to be swapped out for other predetermined characters in a consistent way. If you're dealing with the alphabet, each letter would have a corresponding number or character assigned to it. For example, A could be 1, and B could be 2.
Ciphertext Attacks
When committing a ciphertext attack, attackers will usually try to retrieve the decryption code. It’s often pretty difficult to do, but not entirely impossible.
There are two different types of ciphertext attacks:
Cryptanalysis
This is the process by which attackers will try to gain access to and read the information on hand without actually knowing the key to decipher it.
Brute-Force Attack
In a brute-force attack, hackers will play a game of numbers by trying out different keys in the hopes that one of them might be correct. Of course, the longer your decryption key, the more secure your data will be.
Final Thoughts on Ciphertext in Cybersecurity
The concept of ciphertext is pretty straightforward, and it provides a great way to protect private and sensitive information by encryption and decryption. Maintaining the integrity of confidential information and data is of the utmost importance to Sangfor and providing advanced security options that meet your needs is our main goal. Contact Sangfor today for all your cybersecurity needs.
Contact Us for Business Inquiry